UXP Rule Structure
XML Rule Blocks
The original access and mitigation policies visual presented gave names in categories and icons for description purposes. In UXP Technology, a rule structure is a set of parameters that are used in constructing a UXP Identity. From the implementation perspective, the Workflow Guide/Section 3.1.2 Rule Presets defines the rules in table format.
UXP Rule Structure
XML Rule Blocks
The original access and mitigation policies visual presented gave names in categories and icons for description purposes. In UXP Technology, a rule structure is a set of parameters that are used in constructing a UXP Identity. From the implementation perspective, the Workflow Guide/Section 3.1.2 Rule Presets defines the rules in table format.
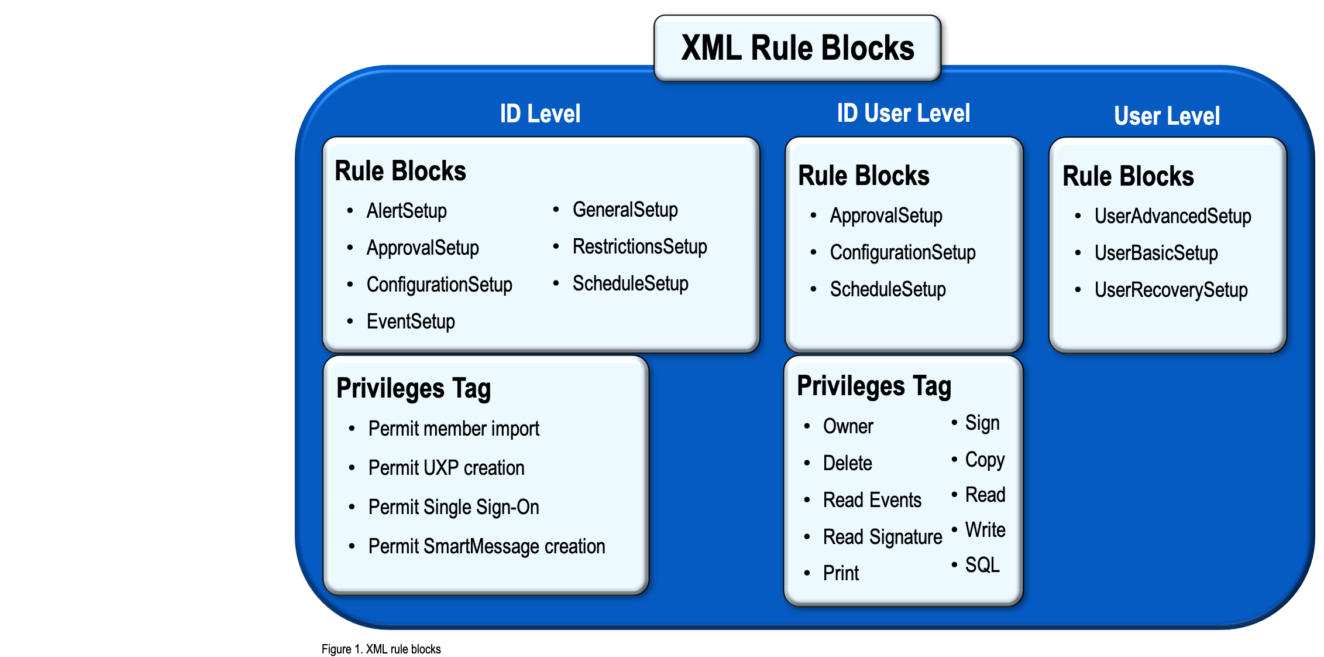
XML Rule Blocks and Privileges
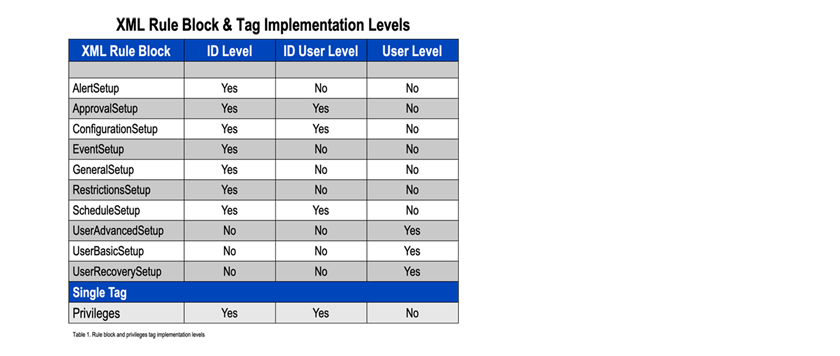
XML rule blocks and privileges are implemented at three levels, ID, ID User and User. Table 1 below shows the rule block and privilege matrix.
Overview
The ID Level rule blocks apply rules equally to all permitted Users.
- AlertsSetup: Alert attributes control the types of information included in a message as well as where the messages are sent, i.e. email address or SMS. Alert message generation is controlled by the UXP Object.
- ApprovalSetup: Approval attributes define where to send an external access-authorization passcode. This passcode must be provided to the User at access time to complete authentication.
- ConfigurationsSetup: Configuration attributes consist of two types of information, hardware and network location. Hardware and network can be used together as a configuration or individually as restriction attribute.
- EventSetup: EventSetup controls how UXP Object activities are recorded. Various event actions may trigger an entry into the internal UXP Object event log. The event log entries can also be recorded externally in a file or repository.
- GeneralSetup: General attributes control time and access limits for a UXP Object. Examples include such attributes as total number of UXP Object accesses or maximum time for the Object being idle.
- RestrictionsSetup: Restriction attributes assign actions to authentication scenarios. These attributes allow a variety of controls to be set.
- ScheduleSetup: Schedule attributes define time-frame and day-of-the-week access restrictions. As a default, a schedule without restrictions is set up.
- Privileges: Privileges in the XML are represented as a single tag at the ID Level. These privileges define how the ID Definition is utilized. The privileges apply equally to all permitted Users.
The ID User Level rule blocks apply specific rules individually to a permitted User.
- ApprovalSetup: Approval attributes define where to send an external access-authorization passcode. This passcode must be provided to the User at access time to complete authentication.
- ConfigurationsSetup: Configuration attributes consist of two types of information, hardware and network location. Hardware and network can be used together as a configuration or individually as restriction attribute.
- ScheduleSetup: Schedule attributes define time-frame and day-of-the-week access restrictions. As a default, a schedule without restrictions is set up.
- Privileges: Privileges in the XML are represented as a single tag at the ID User Level. These privileges define how the ID Definition is utilized. The ID User Level privileges apply specific privileges individually to a permitted User.
The User Level rule blocks apply User-owned rules for a User Definition.
- UserAdvancedSetup: The User Advanced attributes add private actions during the authentication process.
- UserBasicSetup: The User Basic attributes are actions to help minimize the impact of mistakes during authentication.
- UserRecoverySetup: The Recovery attributes allows for tolerance settings for correct and incorrect Responses.