UXP Technology Cornerstone
The UXP Object is a portable protocol used to protect data in a self-managed, one-of-a-kind entity. UXP Technology blends proprietary UXP Intelligence and a unique protection scheme with any size dataset. The result is a UXP Object.
Empowered with UXP Technology, the UXP Object self-protects and self-governs its own access and mitigation activity. These activities are defined by the data-owner using the owner’s pre-determined policies.
File Format
After a UXP Object is created, it appears as an inert, binary file showing a *.uxp extension. The UXP Object is unidentifiable unless proximal to UXP Technology. Without proximity, a UXP Object simply looks ordinary and nondescript on any OS and can be easily designated as junk.
Internal Components
Beginning at a high level, the UXP Object contains the core components mentioned above along with keys and data.
The UXP Identity is a special purpose UXP Object that is required for UXP Object generation. As a pre-requisite, the UXP Identity provides necessary components that empower the UXP Object to be intelligent and proactive at an access attempt and while the data is in-use.
Virtual File System
The Virtual File System stores and manages within the UXP Object the following (including headers):
- KCL Code
- External data as files
- Internal metadata
- Event logs
- Other elements
Within the system, the files are segmented into pages. Each file is individually and uniquely protected with encryption and cloaking. Figure 2 below shows a simulation of an Object’s Virtual File System.
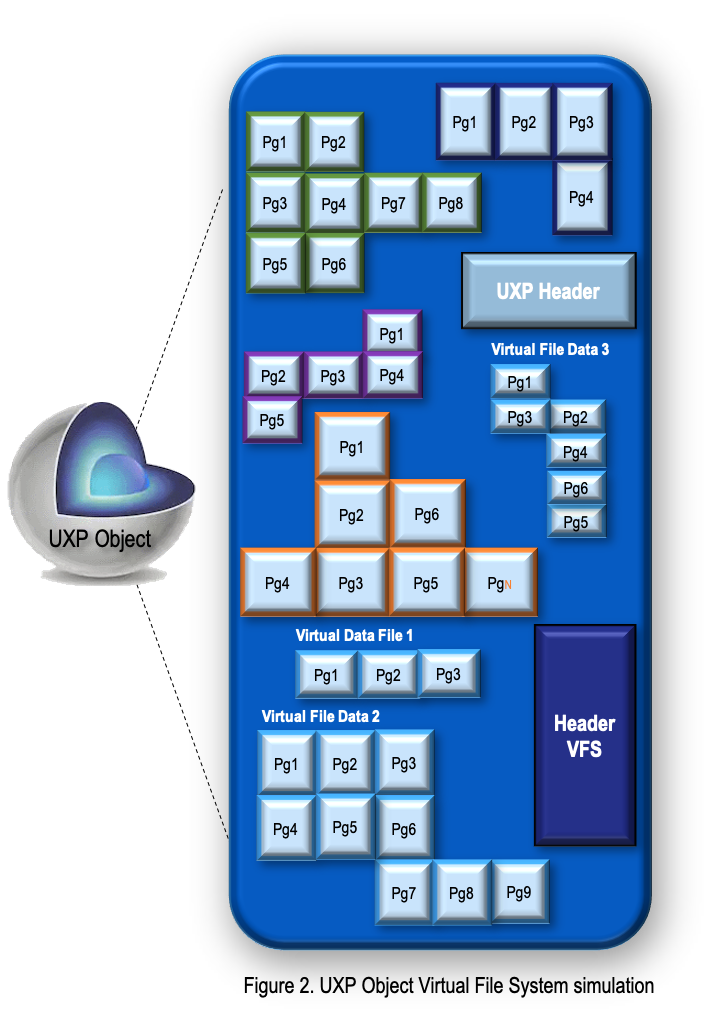
Virtual File System supports a directory structure, individual files/folders or other data of any type.
Directory Structure: A directory structure can contain other virtual files as well as virtual sub-directories. This feature may require additional license privilege.
Data Type: Data can be any user-specified type, such as *.mp4, *.mp3, *.txt, etc. The virtual file can originate from either an existing file or an in-memory buffer. The file system can contain anything that normally goes into a conventional file system. The file system is only limited in size by the operating system itself.
On-Disk Storage Structures:
- Write Once UXP Architecture
- A file system used for storing and protecting data that does not change, e.g., *.mp3 or*.mp4 files.
- Read/Write UXP Architecture
- A file system used for storing data of any type that may change throughout its life cycle.
- Database Tables (available only on Read/Write) are specific storage structures for storing and managing SQLite related database tables and files.
KCL Code: UXP Object Intelligence
The KCL Code originates from the UXP Identity. Acting as a light-weight executable embedded in the UXP Object, this UXP proprietary program is written in a C-like language; the KCL Code is the UXP Object’s Intelligence.

Unique to each UXP Identity, the KCL Code consists of User Definitions and access and mitigation policies .
The KCL Code is also integral in the UXP Object’s encryption key production. These keys are randomly generated by the UXP Engine, another proprietary engine external to the Object.
Additionally, the KCL Code manages all encryption keys internally throughout the Object’s life cycle. Keys are embedded unseen in the Object and protected using a proprietary, recursive UXP protection scheme.
As an executable, the KCL Code requires proximity to UXP Technology, specifically the UXP Engine. The UXP Engine provides the executable environment for the KCL Code. Otherwise, the KCL Code sits dormant and undetectable in the inert UXP Object.
Note: For additional information on the KCL Code, see the KCL Guide.
Internal Metadata
The internal metadata contains all the virtual file system data. All other user-specific data is stored as virtual data files.
UXP Header
Every UXP Object contains a header that allows the UXP Engine to identify the entity as valid UXP Object. If a header isn’t found or read, then the entity is not considered a valid UXP Object.
Encryption Keys
Standard AES-256 GCM encryption is involved in the UXP protection scheme. Added proprietary algorithms generate an embedded, self-contained key management system within the UXP Object. Generated when data is protected, encryption keys are cloaked, inaccessible and never shared.
The KCL Code participates in generating the encryption keys during UXP Object creation. Keys are randomly generated without exposure and contained hidden within the UXP Object. External key management becomes obsolete because the KCL Code manages the keys.
Data
Data can be any data type or size because data is treated as an array of bytes. Data, as shown in Figure 1 above, is optional within a UXP Object. An Object can be authenticated and opened to add data at a later time.
When the data is extracted from the UXP Object, the data looks the same as it did when the data was last protected in the UXP Object.